Challenge Ratting: 2
Skills: Cybersecurity Analytics +1
In the vast sea of your inbox, you might think you’re just angling for important emails, but lurking beneath the surface are some slippery characters looking to hook you in a net of deception. Phishing emails are like crafty anglers, casting their baited lines with the hopes of reeling in unsuspecting victims. They’ve become quite the masters of disguise, often dressing up as legitimate messages, and unless you know how to bait back, you’re in for a rough tide. But don’t worry, because in this article, we’re here to teach you the ropes and show you how to fish out those phishy messages. So grab your virtual fishing rod, and let’s embark on a journey to become the ultimate inbox angler – ready to catch, release, and stay cyber-safe!
I recently had the opportunity to peek behind the curtain of Mastercard’s security operations, focusing specifically on their anti-phishing practices. As a global financial giant, Mastercard is acutely aware of the risks associated with phishing attempts, and preventing data breaches is a top priority. But before we dive into their measures, let’s start with the basics.
Phishing, as defined by Merriam-Webster, the practice of tricking Internet users (as through the use of deceptive email messages or websites) into revealing personal or confidential information which can then be used illicitly
To ensure that their employees remain vigilant against such threats, Mastercard periodically crafts and sends out phishing emails as part of an internal testing regimen. I was fortunate enough to create and send one of these simulated phishing emails myself.
Scenario
I was initially presented with a rudimentary phishing email to assess my ability to identify overt signs of phishing and let me tell you, they were unmistakable.
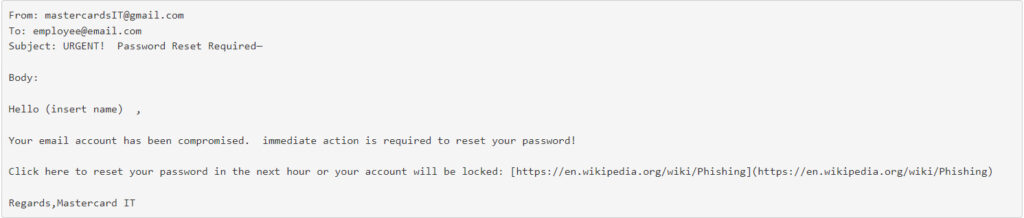
Upon closer inspection, a multitude of red flags became apparent in this phishing email. To start, the sender’s address was a Gmail account, which immediately raised suspicion as it was meant to appear as an internal communication. Also, the sender misspelled Mastercard
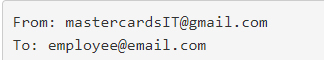
Moving on, the subject line carried the word ‘URGENT,’ a classic tactic employed to grab the recipient’s attention and inject a sense of pressing importance.
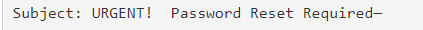
Delving into the email’s body, the urgency was further intensified with phrases like ‘compromised’, ‘immediate action is required’, and ‘reset your password within the next hour, or your account will be locked.’ Consequences were explicitly threatened if one failed to comply, creating a psychological push towards clicking the enclosed link.
Another telltale sign of this email’s dubious nature was the evident grammar issues. It was riddled with misspelled words, questionable punctuation, words left in lowercase when they should be capitalized, and an excessive number of spaces between words. All these language problems were clear indications of a scam.
Lastly, scrutinizing the email’s URL, it was evident that the provided link did not match the one advertised in the message. It’s crucial to recognize that the primary objective of phishing emails is to deceive recipients into clicking these malicious links, ultimately granting the sender unauthorized access to sensitive information.
By dissecting these elements, it becomes evident how critical it is to sharpen our ability to detect and defend against phishing attacks.”
The Exercise
Now it was my turn to craft an email. The objective is to make a phishing email that is not only convincing but sheds a light on the techniques that malicious actors employ. It’s important to emphasize that this exercise was conducted strictly for educational purposes, with a strong focus on responsible usage.
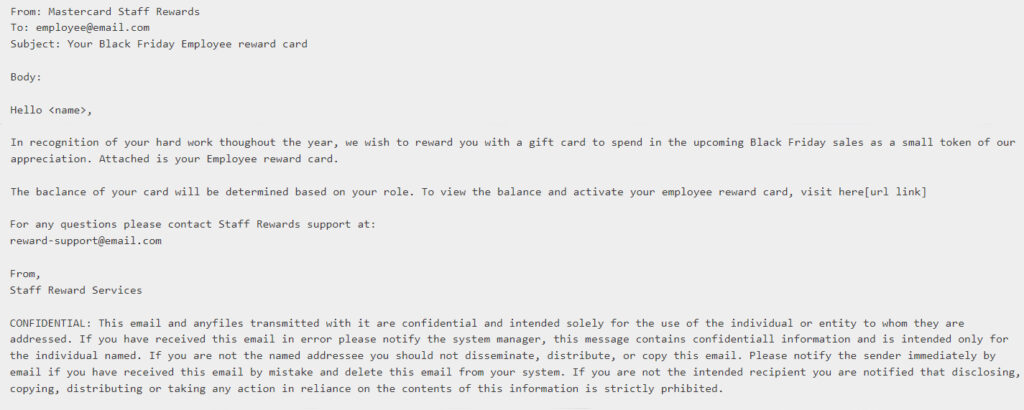
Our first task was to correct the misspelling of ‘Mastercard,’ as authenticity hinges on meticulous details. Next, we had to lend an air of legitimacy to the email, making it appear to emanate from a trustworthy source. Instead of resorting to fearmongering tactics to entice clicks, we aimed for a more enticing subject line that would pique the reader’s curiosity and desire for rewards, aligning with their hard work ethic.
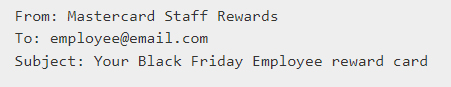
Within the body of the email, we took personalization to another level by tailoring the content to upcoming events, in this case, a thrilling Black Friday event. Embedding the link in plaintext and seamlessly integrating it into the sentence structure made it substantially more clickable. To enhance credibility, we introduced another email address in the body, serving the dual purpose of legitimizing the communication and expanding the email’s content, which is a known tactic used by cybercriminals.
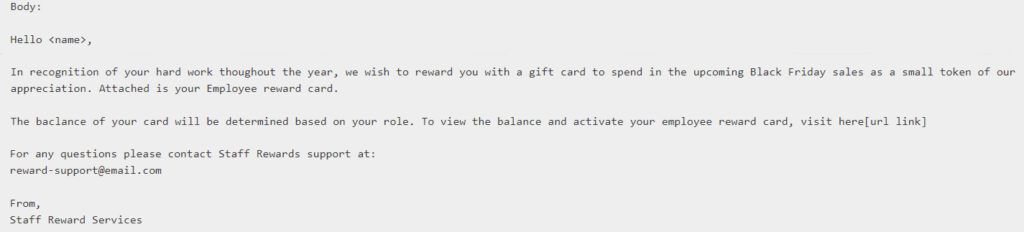
To add the finishing touch of authenticity, we included a confidential disclaimer towards the end of the email. In truth, few recipients meticulously scrutinize this portion, making it an often overlooked yet impactful element in establishing credibility. The process of crafting such an email not only offers insights into the deceptive techniques employed by cybercriminals but also underscores the critical importance of vigilance in the face of such persuasive phishing attempts.
Let’s delve into the findings of our recent phishing campaign and analyze the results to gain valuable insights into team susceptibility.
Within the data lies a table offering a glimpse into which teams might be more prone to falling victim to a phishing email compared to others. It’s essential to understand the metrics utilized in this analysis:
- Email Open Rate: This metric showcases the percentage of individuals who opened the phishing email out of the total number of recipients.
- Email Click-Through Rate: It represents the percentage of people who not only opened the email but also clicked on the malicious link embedded within it.
- Phishing Success Rate: This critical metric reveals the percentage of individuals who went a step further by providing personal information after clicking the malicious link.
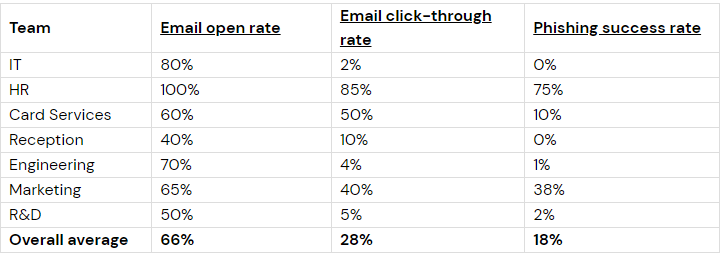
Now that you’ve meticulously scrutinized the data, it’s evident that both the HR and Marketing teams have demonstrated the highest Phishing Success Rate. With this insight in mind, it’s imperative that we take proactive steps to strengthen their cybersecurity awareness and defenses. As part of our response strategy, let’s embark on creating an impactful presentation tailored specifically for these two teams. We aim to provide them with the necessary awareness and training materials to bolster their resilience against phishing attacks. Recognizing that traditional training methods may not always captivate our employees, let’s strive to craft a presentation that is clear, concise, and engaging. We’ll delve into the fundamentals of phishing, explaining what it entails and highlighting common tactics employed by cybercriminals. To ensure maximum effectiveness, let’s tap into a myriad of creative resources, leveraging interactive elements and real-world examples to drive home the importance of vigilance in safeguarding our organization’s sensitive data. By empowering our teams with knowledge and practical insights, we can collectively elevate our security posture and mitigate the risks posed by phishing threats.
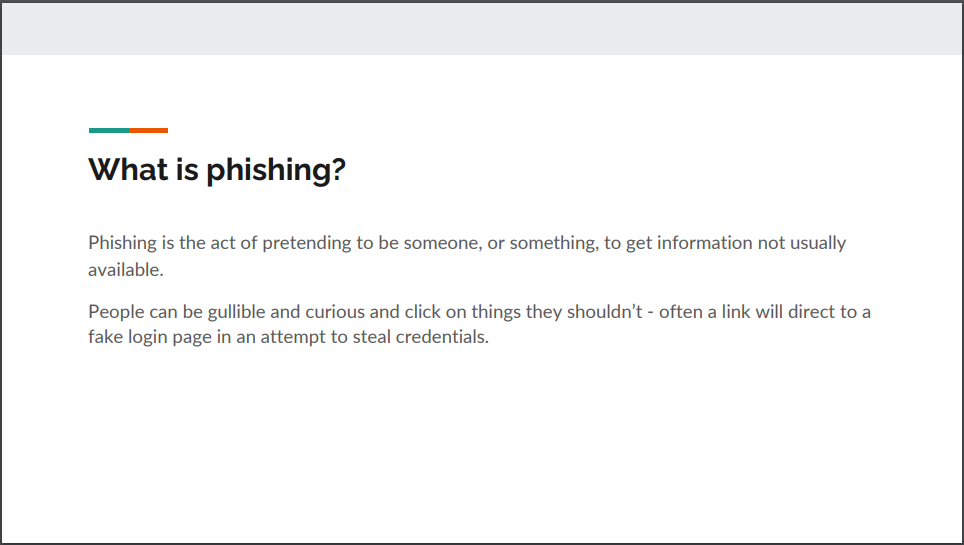
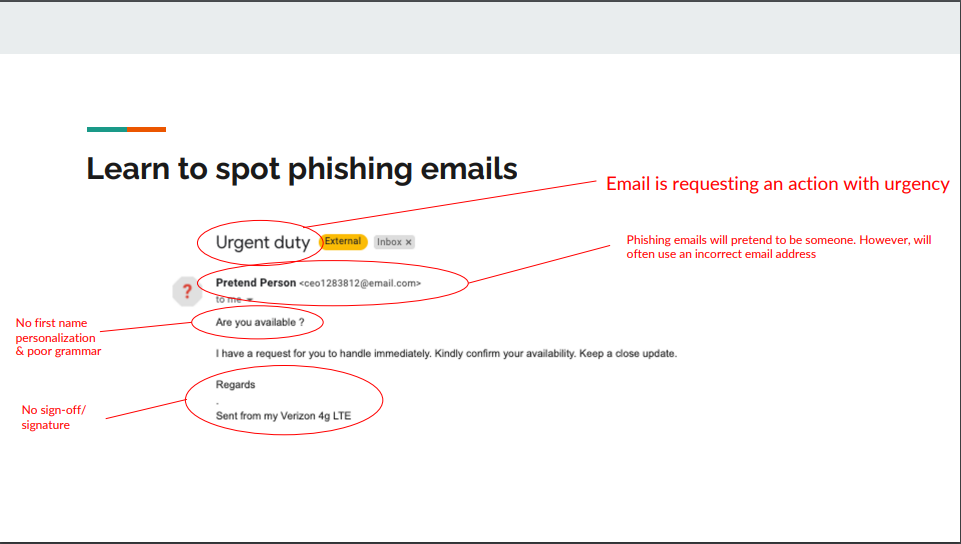

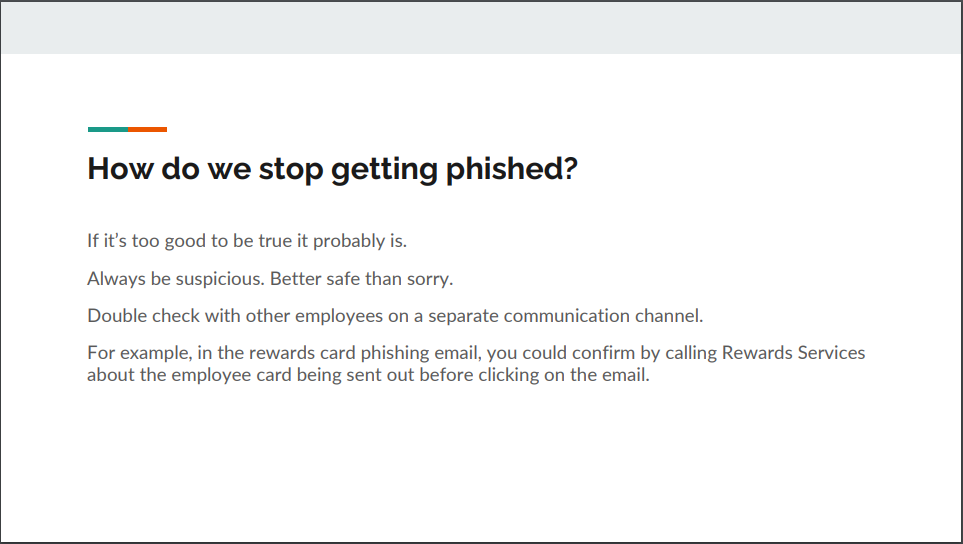
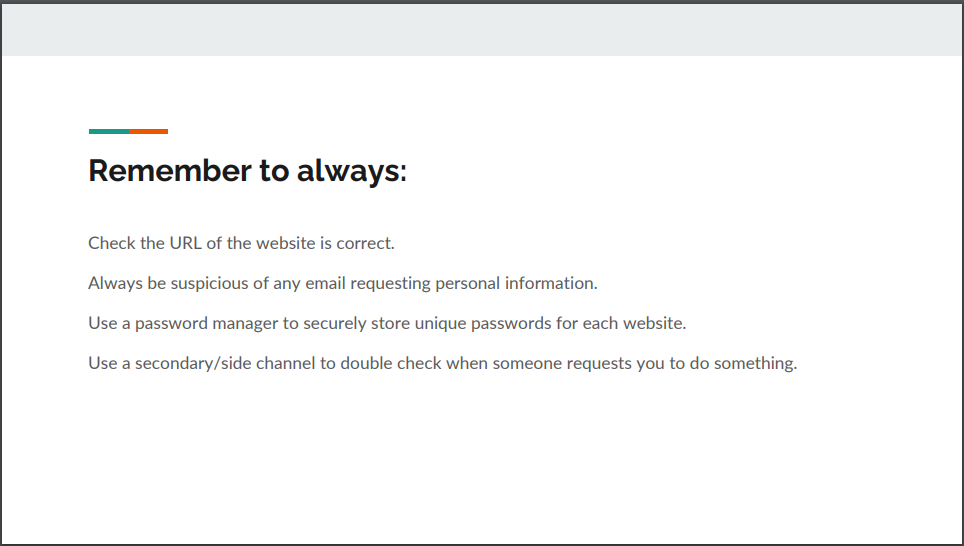
In reflecting on the example presentation crafted for the HR and Marketing teams, several key takeaway points emerge, underscoring the effectiveness of its design:
Firstly, the presentation ingeniously integrates contextual and visual examples, offering practical insights into identifying phishing emails. By illustrating common tactics employed by cybercriminals, such as spoofed sender addresses and suspicious links, employees are equipped with the discernment needed to thwart potential threats.
Secondly, clarity and conciseness are paramount features of the presentation. Through a wise selection of content and a streamlined delivery, complex concepts are condensed into digestible nuggets of information. The strategic incorporation of visuals further enhances comprehension, ensuring that vital security messages resonate with the audience.
Lastly, the presentation ends with clear and concise action points, empowering employees to take proactive steps in fortifying their cybersecurity defenses. From exercising caution when clicking on links to promptly reporting suspicious emails, these actionable directives provide a roadmap for mitigating the risks posed by phishing attacks.
In essence, the example presentation serves as a testament to the efficacy of employing innovative and engaging approaches to cybersecurity training. By embracing contextual examples, clarity, and actionable insights, organizations can cultivate a culture of vigilance and resilience, safeguarding against the ever-evolving landscape of cyber threats.
Final Thoughts
As we reel in our journey through the deceptive depths of phishing emails, let’s anchor in the wisdom that vigilance is our best bait against these cyber predators. Inspired by Mastercard’s proactive defenses and our own foray into crafting a phishing message, it’s clear that the key to safeguarding our digital domains lies in awareness and education. Each suspicious email we navigate, every link we scrutinize, strengthens our defenses, making us less likely to be ensnared by the lures of online tricksters.
Let this voyage remind us that in the vast, often murky waters of the internet, being an informed and cautious navigator is paramount. By fostering a culture of skepticism and empowering ourselves with knowledge, we turn the tide against cyber threats. So, as you sail back into the sea of your inbox, remember, that the best catch is a safe and secure digital experience. May your cyber fishing expeditions be fruitful, and your digital waters free of phishing nets.
